CMMC-Konformität: Was Sie über die endgültige Regelung von 2024 wissen müssen
Das Verteidigungsministerium (DoD) hat seine endgültige Regelung zur Einhaltung des CMMC veröffentlicht, was eine erhebliche Änderung der Cybersicherheitsanforderungen für Verteidigungsunternehmen bedeutet. In diesem umfassenden Leitfaden erfahren Sie alles, was Sie über die neue Regelung wissen müssen. CMMC 2.0-Rahmenwerk und den Zeitplan für die Umsetzung.

Inhalt
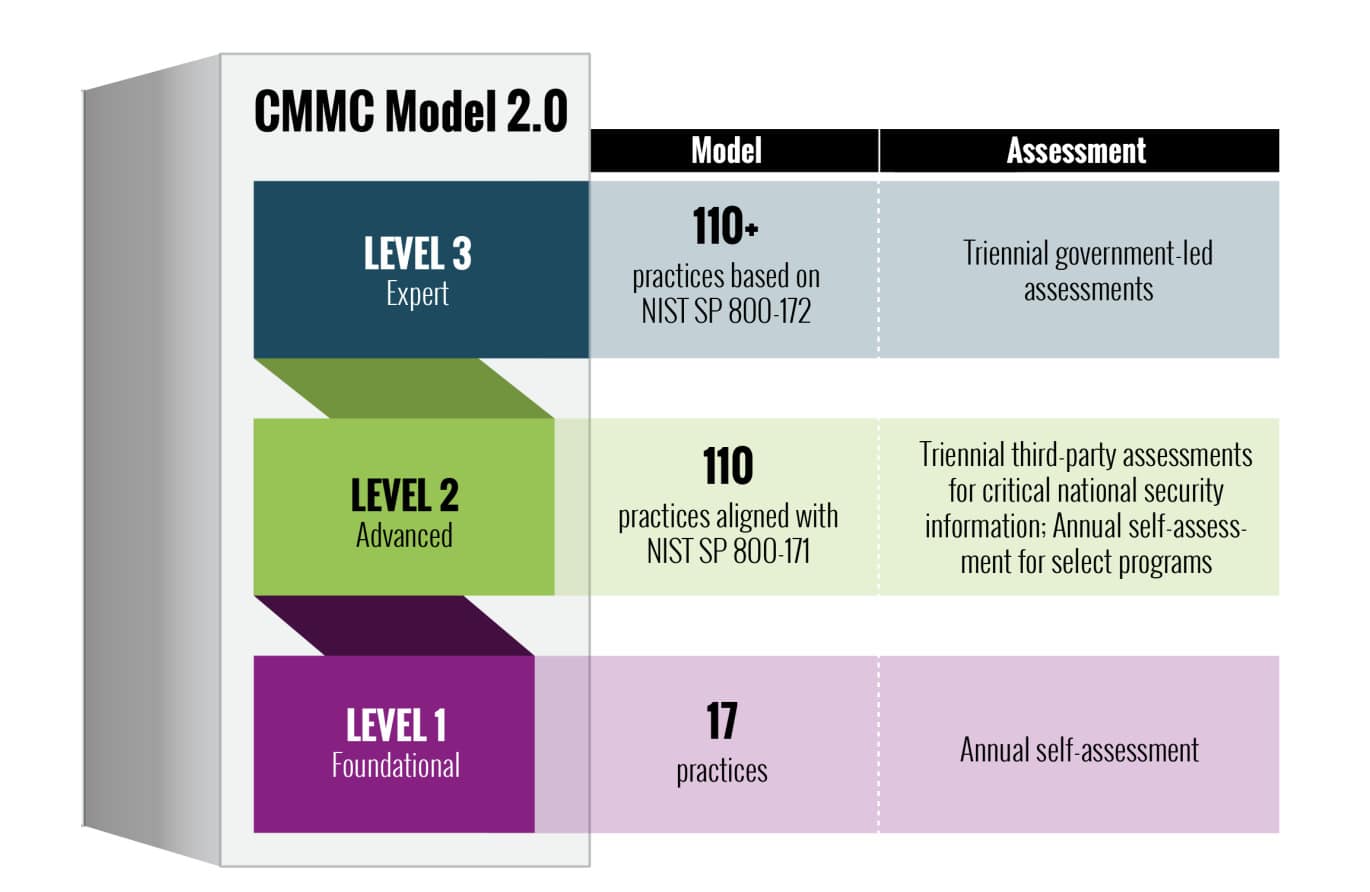
CMMC-Compliance-Level verstehen
Das neue CMMC-Compliance-Framework vereinfacht das bisherige Fünf-Ebenen-System auf drei unterschiedliche Ebenen:
- Level 1 – Grundkenntnisse:
- Erfordert einen grundlegenden Schutz von Federal Contract Information (FCI) durch 15 grundlegende Sicherheitskontrollen. Diese Stufe ist für Auftragnehmer gedacht, die weniger vertrauliche Informationen verarbeiten, und konzentriert sich auf wesentliche Cybersicherheitspraktiken wie Zugriffskontrolle, grundlegende Systemwartung und grundlegende Datenschutzprotokolle. Organisationen auf dieser Stufe befassen sich normalerweise mit Informationen zu Bundesverträgen, die zwar wichtig sind, aber nicht den erhöhten Schutz erfordern, der für kontrollierte, nicht klassifizierte Informationen erforderlich ist.
- Level 2 – Fortgeschritten:
- Erfordert die Implementierung von 110 Sicherheitskontrollen aus NIST SP 800-171 für den Umgang Kontrollierte nicht klassifizierte Informationen (CUI). Diese Zwischenstufe erhöht die Sicherheitsanforderungen erheblich und umfasst erweiterte Zugriffskontrollen, Notfallreaktionspläne, umfassende Sicherheitsschulungen und robuste Systemüberwachungsfunktionen. Unternehmen müssen einen angemessenen Schutz vor CUI in ihrer gesamten Infrastruktur, einschließlich physischer und digitaler Assets, nachweisen und gleichzeitig eine detaillierte Dokumentation ihrer Sicherheitspraktiken führen.
- Level 3 – Experte:
- Fügt 24 zusätzliche Sicherheitskontrollen aus NIST SP 800-172 für maximalen Schutz hinzu. Diese höchste Stufe ist Auftragnehmern vorbehalten, die mit den sensibelsten, nicht klassifizierten Informationen umgehen, und erfordert anspruchsvolle Sicherheitsmaßnahmen wie erweiterte Verschlüsselungsprotokolle, kontinuierliche Sicherheitsüberwachung, regelmäßige Penetrationstests und verbesserte Fähigkeiten zur Reaktion auf Vorfälle. Unternehmen müssen außerdem spezielle Sicherheitskontrollen für das Risikomanagement in der Lieferkette implementieren und die Fähigkeit nachweisen, fortgeschrittene, anhaltende Bedrohungen zu erkennen und darauf zu reagieren.
Wichtiger Zeitplan für die CMMC-Konformität und Implementierung
Ab 2025 müssen alle Rüstungsunternehmen bei der Auftragsvergabe die Einhaltung des CMMC nachweisen. Das Programm umfasst:
- Eine dreijährige Übergangsphase soll einen reibungslosen Übergang gewährleisten. In dieser Phase können Auftragnehmer die erforderlichen Sicherheitskontrollen schrittweise implementieren und sich den erforderlichen Prüfungen unterziehen, ohne das Risiko einer sofortigen Disqualifikation durch den Auftrag einzugehen. In dieser Phase können Organisationen Sicherheitsverbesserungen angemessen budgetieren, Personal schulen und robuste Dokumentationsprozesse einrichten, während sie gleichzeitig weiterhin die Möglichkeit haben, Angebote für DoD-Aufträge abzugeben.
- Umsetzung der DFARS-Regeländerungen bis Mitte 2025, die die CMMC-Anforderungen formell in den Beschaffungsvorschriften für Verteidigungsgüter kodifizieren. Diese Änderungen werden sich auf alles auswirken, von der Vertragssprache bis zu den Angebotsanforderungen, und grundlegend verändern, wie Auftragnehmer die Einhaltung der Cybersicherheit in ihren Geschäftsabläufen des Verteidigungsministeriums angehen. Organisationen müssen diese neuen regulatorischen Anforderungen verstehen und sich an sie anpassen, während sie gleichzeitig ihre bestehenden Sicherheitsprotokolle beibehalten.
- Jährliche Bestätigungsanforderungen zur Aufrechterhaltung des Compliance-Status, bei denen die Geschäftsleitung die fortlaufende Einhaltung aller geltenden Sicherheitskontrollen durch die Organisation bestätigt. Dieser Prozess umfasst die Dokumentation aller Sicherheitsvorfälle, Änderungen an der Systemarchitektur und Abhilfemaßnahmen im Laufe des Jahres. Organisationen müssen außerdem Nachweise über eine laufende Compliance-Überwachung und regelmäßige Sicherheitsbewertungen vorlegen, um ihre Bestätigungen zu untermauern.
Anforderungen an die CMMC-Konformitätsbewertung
Der Bewertungsprozess variiert je nach Niveau:
- Stufe 1:
- Selbstbewertung ist für Auftragnehmer zulässig, die grundlegende FCI-Vorgänge durchführen. Dabei müssen die Organisationen ihre Implementierung der 15 grundlegenden Sicherheitskontrollen gründlich bewerten. Dazu gehört die Führung einer detaillierten Dokumentation der Kontrollimplementierung, regelmäßige interne Audits und die Einrichtung eines Prozesses zur Behebung aller festgestellten Lücken. Organisationen müssen außerdem Richtlinien und Verfahren entwickeln und pflegen, die ihr Verständnis und ihre Anwendung dieser Kontrollen in ihrem spezifischen Betriebskontext belegen.
- Stufe 2:
- Mischung aus Selbstbewertung und Zertifizierung durch Dritte, abhängig von der Sensibilität der behandelten CUI. Organisationen, die eine Zertifizierung durch Dritte benötigen, müssen sich umfassenden Bewertungen durch autorisierte C3PAOs unterziehen, die sowohl die technischen Implementierungen als auch die verfahrensmäßige Einhaltung aller 110 Sicherheitskontrollen bewerten. Dazu gehören detaillierte Untersuchungen der Systemkonfigurationen, der Richtliniendokumentation, der Schulungsunterlagen des Personals und der Fähigkeiten zur Reaktion auf Vorfälle. Unternehmen, die eine Selbstbewertung durchführen dürfen, müssen weiterhin eine strenge Dokumentation und Nachweise der Einhaltung führen.
- Stufe 3:
- Obligatorische Bewertung durch Dritte durch DIBCAC, die die strengste Bewertung aller Sicherheitskontrollen umfasst, einschließlich der zusätzlichen 24 Anforderungen von NIST SP 800-172. Diese Bewertungen umfassen eingehende technische Tests, eine umfassende Überprüfung der Dokumentation und die Bewertung erweiterter Sicherheitsfunktionen wie Bedrohungssuche und Sicherheitsorchestrierung. Organisationen müssen nicht nur die Implementierung, sondern auch die betriebliche Wirksamkeit aller Sicherheitskontrollen durch praktische Übungen und reale Szenarien nachweisen.
Aktuelle Daten zeigt eine erhebliche Lücke in der Compliance-Wahrnehmung: Während 75% der Unternehmen glaubten, sie seien durch Selbstbewertung CMMC-konform, erfüllten nur 4% die Anforderungen tatsächlich, als sie von Dritten bewertet wurden.
Wichtige Überlegungen zur CMMC-Konformität für Auftragnehmer
Anforderungen an Subunternehmer
- Alle Subunternehmer müssen die entsprechenden CMMC-Konformitätsstufen einhalten
- Hauptauftragnehmer sind für die Überprüfung der Einhaltung der Vorschriften durch die Subunternehmer verantwortlich.
- Flow-Down-Anforderungen gelten entlang der gesamten Lieferkette
Bewertung und Zertifizierung
- Zertifizierungen durch Dritte beginnen im Dezember 2024
- Aktions- und Meilensteinpläne (POA&Ms) für Auftragnehmer der Stufen 2 und 3 zulässig
- 180-tägiges Zeitfenster zum Abschluss von POA&Ms nach bedingter Zertifizierung
Risikomanagement
- Jährliche Bestätigungen durch hohe Beamte
- Haftung nach dem False Claims Act für ungenaue Konformitätserklärungen
- Neubewertungen nach wesentlichen Systemänderungen oder Fusionen erforderlich
Vorbereitung auf die CMMC-Konformität
Organisationen sollten:
- Bestimmen Sie den erforderlichen CMMC-Konformitätsgrad
- Planen Sie Bewertungen durch Dritte frühzeitig ein, da ein Rückstand zu erwarten ist
- Überprüfen und aktualisieren Sie aktuelle Cybersicherheitspraktiken
- Implementieren Sie die erforderlichen Sicherheitskontrollen
- Dokumentieren Sie die Compliance-Bemühungen und führen Sie ordnungsgemäße Aufzeichnungen
Fazit
Die Einhaltung des CMMC stellt eine entscheidende Änderung der Cybersicherheitsanforderungen des Verteidigungsministeriums dar. Da die Umsetzung ab 2025 obligatorisch ist, müssen Auftragnehmer jetzt handeln, um sicherzustellen, dass sie alle erforderlichen Anforderungen erfüllen und weiterhin wettbewerbsfähig bleiben, wenn es um Aufträge des Verteidigungsministeriums geht.
Um die aktuellsten Informationen zu den CMMC-Konformitätsanforderungen und Implementierungsrichtlinien zu erhalten, sollten Auftragnehmer regelmäßig die offiziellen Ressourcen des Verteidigungsministeriums konsultieren und die Einbindung zertifizierter Konformitätsgutachter in Erwägung ziehen.
FAQ
Was ist der Unterschied zwischen CMMC Version 1 und 2?
CMMC Version 1 hatte fünf Ebenen mit vielen detaillierten Kontrollen, die auf jeder Ebene Bewertungen durch Dritte erforderten. CMMC Version 2 vereinfacht dies, indem es die Ebenen auf drei reduziert, sich an NIST-Standards anpasst und sich auf Selbstbewertungen für niedrigere Ebenen und Bewertungen durch Dritte für höhere Ebenen konzentriert, wodurch die Einhaltung einfacher und zugänglicher wird.
Welches CMMC-Compliance-Level benötigt meine Organisation?
Ihr erforderliches CMMC-Level hängt von der Art der von Ihnen verarbeiteten Informationen ab. Organisationen, die mit Federal Contract Information (FCI) arbeiten, benötigen Level 1 (15 Kontrollen). Wenn Sie mit Controlled Unclassified Information (CUI) arbeiten, benötigen Sie Level 2 (110 Kontrollen). Organisationen, die mit den sensibelsten nicht klassifizierten Informationen arbeiten, benötigen Level 3, das 24 erweiterte Sicherheitskontrollen aus NIST SP 800-172 hinzufügt.
Wann müssen Rüstungsunternehmen eine CMMC-Zertifizierung erhalten?
Die Einhaltung der CMMC-Vorschriften wird für alle Auftragnehmer des Verteidigungsministeriums ab 2025 verpflichtend. Die Zertifizierung durch Dritte beginnt im Dezember 2024, wobei eine dreijährige Übergangsphase vorgesehen ist, um eine reibungslose Umsetzung zu gewährleisten. Das Verteidigungsministerium wird die Änderungen der DFARS-Regeln bis Mitte 2025 umsetzen und von den Auftragnehmern verlangen, die Einhaltung der Vorschriften bei der Auftragsvergabe nachzuweisen.
