Cumplimiento de CMMC: lo que necesita saber sobre la norma final de 2024
El Departamento de Defensa (DoD) ha publicado su norma final para el cumplimiento de CMMC, lo que marca un cambio significativo en los requisitos de ciberseguridad para los contratistas de defensa. Esta guía completa detalla todo lo que necesita saber sobre la nueva norma. Marco CMMC 2.0 y su cronograma de implementación.

Contenido
- Comprensión de los niveles de cumplimiento de CMMC
- Cronograma de implementación y cumplimiento clave de CMMC
- Requisitos de evaluación de cumplimiento de CMMC
- Consideraciones importantes sobre el cumplimiento de CMMC para contratistas
- Preparación para el cumplimiento de CMMC
- Conclusión
- Preguntas más frecuentes
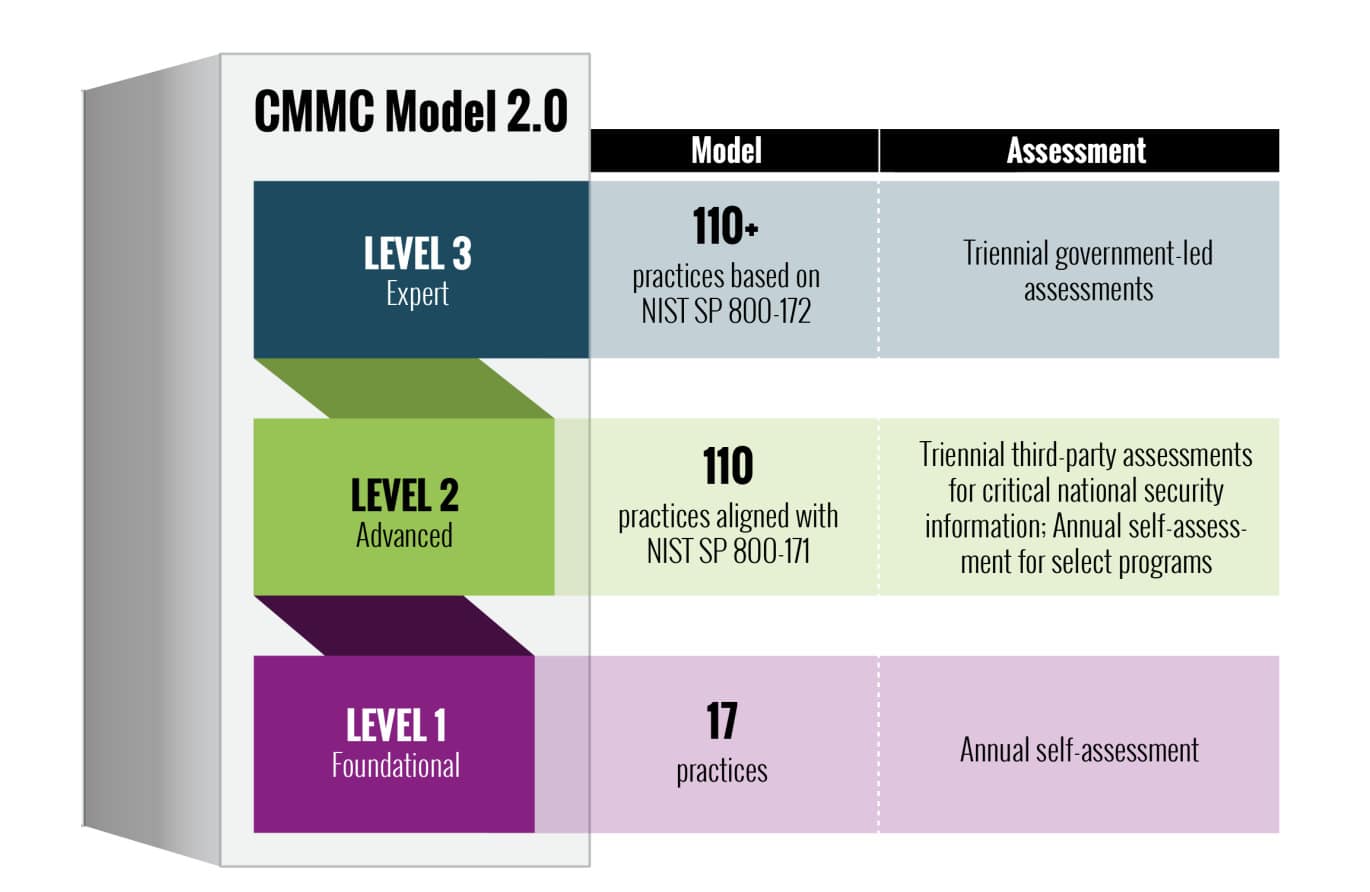
Comprensión de los niveles de cumplimiento de CMMC
El nuevo marco de cumplimiento de CMMC simplifica el sistema anterior de cinco niveles en tres niveles distintos:
- Nivel 1 – Fundacional:
- Requiere protección básica de la información de contratos federales (FCI) a través de 15 controles de seguridad fundamentales. Este nivel está diseñado para contratistas que manejan información menos confidencial y se centra en prácticas esenciales de ciberseguridad, como control de acceso, mantenimiento básico del sistema y protocolos fundamentales de protección de datos. Las organizaciones en este nivel suelen manejar información de contratos federales que, si bien es importante, no requiere la protección mejorada necesaria para la información no clasificada controlada.
- Nivel 2 – Avanzado:
- Exige la implementación de 110 controles de seguridad de NIST SP 800-171 para el manejo Información no clasificada controlada (CUI). Este nivel intermedio aumenta significativamente los requisitos de seguridad para incluir controles de acceso avanzados, planes de respuesta a incidentes, capacitación integral en seguridad y capacidades sólidas de monitoreo del sistema. Las organizaciones deben demostrar una protección adecuada de la CUI en toda su infraestructura, incluidos los activos físicos y digitales, al tiempo que mantienen una documentación detallada de sus prácticas de seguridad.
- Nivel 3 – Experto:
- Añade 24 controles de seguridad adicionales de NIST SP 800-172 para una máxima protección. Este nivel superior está reservado para los contratistas que manejan la información no clasificada más sensible y requiere medidas de seguridad sofisticadas, como protocolos de cifrado avanzados, monitoreo de seguridad continuo, pruebas de penetración periódicas y capacidades mejoradas de respuesta a incidentes. Las organizaciones también deben implementar controles de seguridad especializados para la gestión de riesgos de la cadena de suministro y demostrar la capacidad de detectar y responder a amenazas persistentes avanzadas.
Cronograma de implementación y cumplimiento clave de CMMC
A partir de 2025, todos los contratistas de defensa deberán demostrar el cumplimiento de la CMMC en el momento de la adjudicación del contrato. El programa incluye:
- Un período de implementación gradual de tres años para garantizar una transición sin problemas, durante el cual los contratistas pueden implementar gradualmente los controles de seguridad requeridos y someterse a las evaluaciones necesarias sin correr el riesgo de quedar inmediatamente descalificados para un contrato. Este período permite a las organizaciones presupuestar adecuadamente las mejoras de seguridad, capacitar al personal y establecer procesos de documentación sólidos, manteniendo al mismo tiempo su capacidad para presentar ofertas en contratos del Departamento de Defensa.
- Implementación de los cambios en las normas del DFARS a mediados de 2025, que codificarán formalmente los requisitos de CMMC en las regulaciones de adquisiciones de defensa. Estos cambios afectarán todo, desde el lenguaje del contrato hasta los requisitos de la propuesta, y cambiarán fundamentalmente la forma en que los contratistas abordan el cumplimiento de la ciberseguridad en sus operaciones comerciales del Departamento de Defensa. Las organizaciones deberán comprender y adaptarse a estos nuevos requisitos regulatorios, manteniendo al mismo tiempo sus protocolos de seguridad existentes.
- Requisitos de confirmación anual para mantener el estado de cumplimiento, lo que implica que la alta dirección confirme el cumplimiento continuo de la organización con todos los controles de seguridad aplicables. Este proceso incluye la documentación de cualquier incidente de seguridad, cambios en la arquitectura del sistema y esfuerzos de reparación durante todo el año. Las organizaciones también deben mantener evidencia de monitoreo continuo del cumplimiento y evaluaciones de seguridad periódicas para respaldar sus afirmaciones.
Requisitos de evaluación de cumplimiento de CMMC
El proceso de evaluación varía según el nivel:
- Nivel 1:
- Se permite la autoevaluación para los contratistas que manejan FCI básico, lo que requiere que las organizaciones evalúen exhaustivamente su implementación de los 15 controles de seguridad básicos. Esto incluye mantener una documentación detallada de la implementación de los controles, realizar auditorías internas periódicas y establecer un proceso para abordar cualquier deficiencia identificada. Las organizaciones también deben desarrollar y mantener políticas y procedimientos que demuestren su comprensión y aplicación de estos controles dentro de su contexto operativo específico.
- Nivel 2:
- Combinación de autoevaluación y certificación de terceros, según la sensibilidad de la CUI que se esté manejando. Las organizaciones que requieren certificación de terceros deben someterse a evaluaciones integrales por parte de C3PAO autorizados, quienes evaluarán tanto las implementaciones técnicas como el cumplimiento de los procedimientos de los 110 controles de seguridad. Esto incluye exámenes detallados de las configuraciones del sistema, la documentación de políticas, los registros de capacitación del personal y las capacidades de respuesta a incidentes. Las empresas a las que se les permite realizar autoevaluaciones deben mantener una documentación rigurosa y evidencia de cumplimiento.
- Nivel 3:
- Evaluación obligatoria de terceros por parte de DIBCAC, que implica la evaluación más estricta de todos los controles de seguridad, incluidos los 24 requisitos adicionales de NIST SP 800-172. Estas evaluaciones incluyen pruebas técnicas exhaustivas, revisión exhaustiva de la documentación y evaluación de capacidades de seguridad avanzadas, como búsqueda de amenazas y orquestación de la seguridad. Las organizaciones deben demostrar no solo la implementación, sino también la eficacia operativa de todos los controles de seguridad a través de ejercicios prácticos y escenarios del mundo real.
Datos recientes muestra una brecha significativa en la percepción de cumplimiento: mientras que el 75% de las empresas creían que cumplían con CMMC a través de la autoevaluación, solo el 4% realmente cumplió con los requisitos cuando fueron evaluadas por terceros.
Consideraciones importantes sobre el cumplimiento de CMMC para contratistas
Requisitos del subcontratista
- Todos los subcontratistas deben mantener niveles adecuados de cumplimiento de CMMC
- Los contratistas principales son responsables de verificar el cumplimiento de los subcontratistas.
- Los requisitos de flujo descendente se aplican a lo largo de toda la cadena de suministro.
Evaluación y certificación
- Las certificaciones de terceros comienzan en diciembre de 2024
- Planes de acción e hitos (POA&M) permitidos para contratistas de nivel 2 y 3
- Ventana de 180 días para cerrar los POA&M después de la certificación condicional
Gestión de riesgos
- Afirmaciones anuales requeridas por altos funcionarios
- Responsabilidad de la Ley de Reclamaciones Falsas por declaraciones de cumplimiento inexactas
- Se requieren nuevas evaluaciones después de cambios o fusiones importantes del sistema
Preparación para el cumplimiento de CMMC
Las organizaciones deberían:
- Determinar su nivel de cumplimiento CMMC requerido
- Programe evaluaciones de terceros con anticipación debido a la acumulación de trabajo anticipada
- Revisar y actualizar las prácticas actuales de ciberseguridad
- Implementar los controles de seguridad necesarios
- Documentar los esfuerzos de cumplimiento y mantener registros adecuados
Conclusión
El cumplimiento de CMMC representa un cambio crucial en los requisitos de ciberseguridad del Departamento de Defensa. Con la implementación obligatoria a partir de 2025, los contratistas deben actuar ahora para garantizar que cumplen con todos los requisitos necesarios y mantienen su capacidad para competir por los contratos del Departamento de Defensa.
Para obtener las últimas actualizaciones sobre los requisitos de cumplimiento de CMMC y la guía de implementación, los contratistas deben consultar periódicamente los recursos oficiales del Departamento de Defensa y considerar contratar evaluadores de cumplimiento certificados.
Preguntas más frecuentes
¿Cuál es la diferencia entre la versión 1 y 2 de CMMC?
La versión 1 de CMMC tenía cinco niveles con muchos controles detallados y requería evaluaciones de terceros en cada nivel. La versión 2 de CMMC simplifica esto al reducir los niveles a tres, alineándose con los estándares del NIST y centrándose en las autoevaluaciones para los niveles inferiores y las evaluaciones de terceros para los niveles superiores, lo que hace que el cumplimiento sea más fácil y accesible.
¿Qué nivel de cumplimiento de CMMC necesita mi organización?
El nivel CMMC requerido depende del tipo de información que maneja. Las organizaciones que trabajan con información de contratos federales (FCI) necesitan el nivel 1 (15 controles). Si maneja información controlada no clasificada (CUI), necesitará el nivel 2 (110 controles). Las organizaciones que manejan la información no clasificada más sensible requieren el nivel 3, que agrega 24 controles de seguridad mejorados de NIST SP 800-172.
¿Cuándo deben los contratistas de defensa obtener la certificación CMMC?
El cumplimiento de CMMC se vuelve obligatorio para todos los contratistas del Departamento de Defensa en 2025. Las certificaciones de terceros comienzan en diciembre de 2024, con un período de implementación gradual de tres años para garantizar una implementación sin problemas. El Departamento de Defensa implementará los cambios en las normas DFARS a mediados de 2025, lo que exigirá a los contratistas que demuestren el cumplimiento en el momento de la adjudicación del contrato.
