Come possiamo aiutarvi oggi?
Modifica dell'ufficio locale dal client Web: host approvati dal Centro protezione
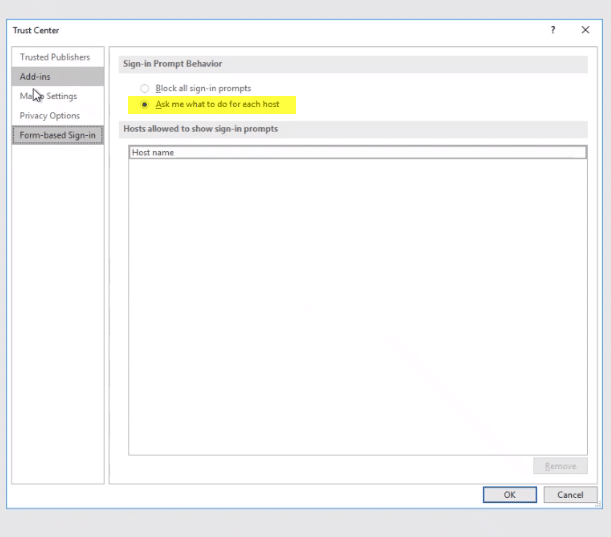
Consentire l'autenticazione basata su moduli
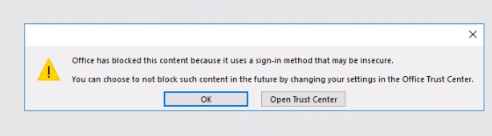
Quando gli utenti aprono documenti di Office in Ufficio locale dal client Web, gli utenti con versioni nuove/aggiornate di Microsoft Office installate localmente potrebbero ricevere un avviso sull'apertura di documenti da fonti online che fanno riferimento al Centro protezione.
Si applica solo a Local Office quando si apre dal Web Client. I client che aprono in Local Office tramite l'unità mappa o Office 365 tramite il Web Client non sono interessati.
Questo non è un problema nel software MyWorkDrive; Microsoft ha introdotto una modifica in Office per richiedere l'approvazione per le fonti di dati di terze parti a partire dal 2020, che è stata lentamente rilasciata alle versioni di Office tramite aggiornamenti. Puoi leggere maggiori dettagli qui:
autenticazione basata su moduli nelle app di Office
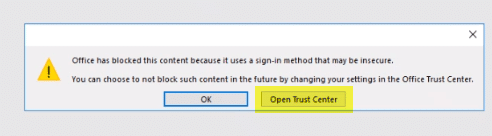
Il processo che l'utente dovrà completare è aprire il centro protezione e scegliere l'opzione di richiesta e autorizzazione per ciascun host.
La prossima volta che l'utente apre un documento, gli verrà richiesto di aggiungere il tuo server MyWorkDrive come posizione approvata
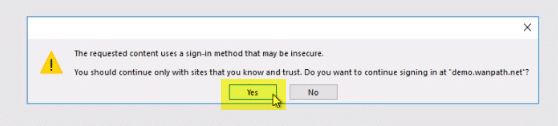
Quindi riceveranno la richiesta di accesso normale/prevista per procedere alla modifica.
Questo è un processo che si effettua una sola volta; una volta che il server è attendibile, l'utente otterrà l'accesso solo allo scadere della sessione.
Potresti essere in grado di inviare origini approvate tramite criteri di gruppo per le macchine aggiunte al dominio o tramite MDM per i dispositivi gestiti.
Impostazione dei percorsi come posizioni attendibili
Impostando una lettera di unità o un percorso come posizione attendibile, si evita l'avviso che un file è stato aperto in sola lettura e che è necessario abilitare la modifica.
Questa operazione può essere eseguita manualmente seguendo le istruzioni sopra indicate per ogni singolo dispositivo, oppure è possibile utilizzare un GPO nei Criteri di gruppo per inviare un aggiornamento ai dispositivi aggiunti al dominio.
Per iniziare, scarica i modelli di Criteri di gruppo per Office da Microsoft.
https://www.microsoft.com/en-us/download/details.aspx?id=49030
Dopo averli scaricati, esegui l'eseguibile e scegli una posizione in cui archiviare i file.
Trasferisci quei file al controller di dominio.
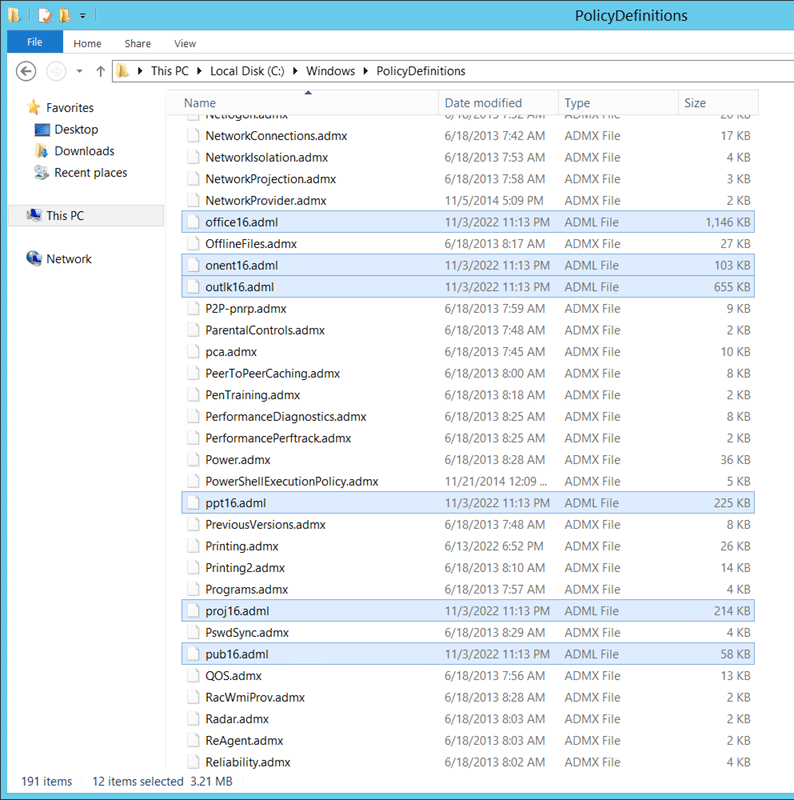
Connettersi al controller di dominio, cercare i file modello dei criteri di gruppo e spostare tutti i file in C:\Windows\PolicyDefinitions sul controller di dominio.
Potresti voler selezionare/copiare solo i file selezionati dall'archivio.
Successivamente, apri la gestione dei criteri di gruppo, crea un nuovo criterio e collegalo all'OU desiderata.
Modifica la nuova policy, quindi vai a:
Configurazione utente > Criteri > Modelli amministrativi > Microsoft Word 2016 > Opzioni di Word > Sicurezza > Centro protezione > e seleziona Percorsi attendibili.
(nota che dovrai impostare questa politica per ogni applicazione di Office)
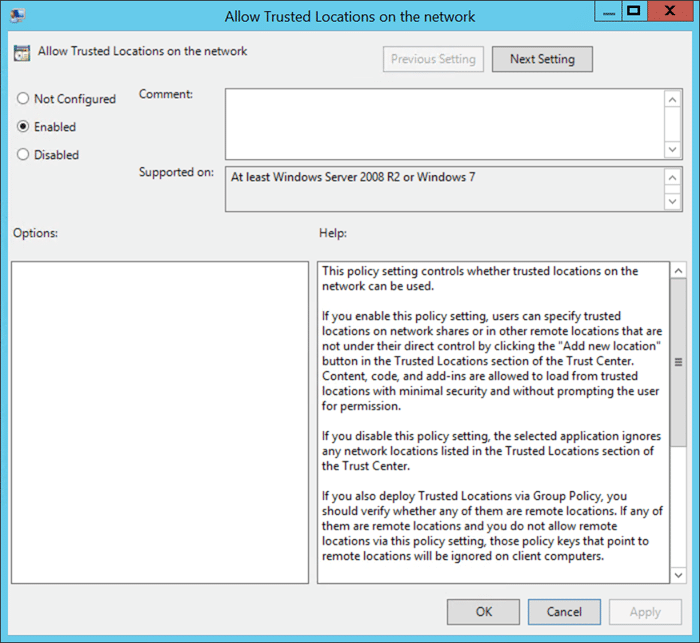
Nel riquadro di destra, vedrai diverse opzioni. L'opzione che ci interessa è "Allow Trusted Locations on the network". Fai doppio clic su quell'opzione e scegli "enable".
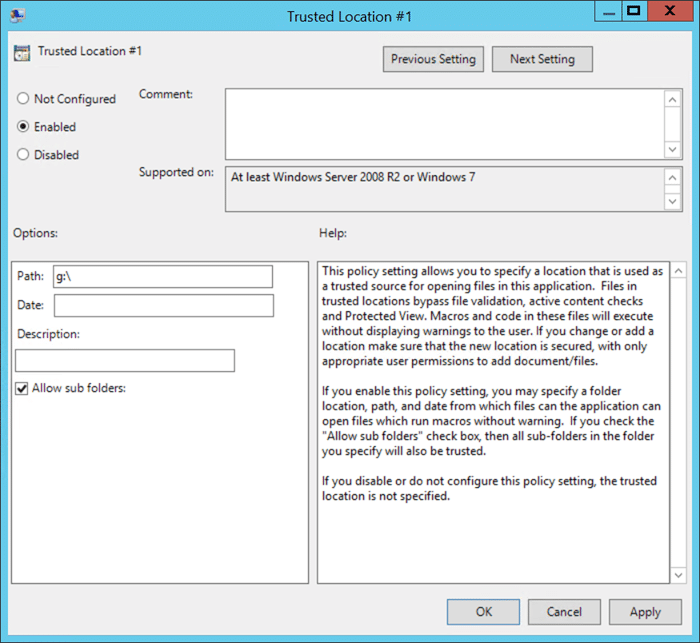
Quindi, aggiungi i tuoi percorsi di rete in posizione attendibile e assicurati che "Consenti sottocartelle:" sia abilitato e seleziona Applica/OK. La lettera dell'unità sarà la lettera o le lettere che stai utilizzando per le condivisioni MyWorkDrive. Se non stai specificando una lettera di unità sul server, il valore predefinito del client è in genere W:, ma può essere modificato lato client.
Ripetere questa procedura per le altre applicazioni di Office scegliendo il modello appropriato.
Dopo aver eseguito questa operazione per tutte le applicazioni, chiudere l'Editor Gestione Criteri di gruppo e assicurarsi che il nuovo criterio di gruppo sia abilitato.
La prossima volta che i tuoi utenti riceveranno i criteri di gruppo, i tuoi percorsi MyWorkDrive dovrebbero essere considerati attendibili e i documenti di Office non verranno più aperti in visualizzazione protetta per impostazione predefinita.