How can we help you today?
Local Office Editing from the Web Client – Trust Center Approved hosts
Allowing Forms Based Authentication
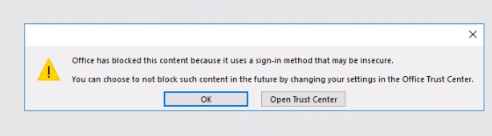
When users open Office documents in Local office from the web client, users with new/updated versions of Microsoft Office installed locally may receive a warning about opening documents from online sources referencing the Trust Center.
It only applies to Local Office when opening from the Web Client. Clients opening in Local Office via the map drive, or Office 365 via the Web Client are unimpacted.
This is not an issue in the MyWorkDrive software; Microsoft introduced a change in Office to prompt for approval for 3rd party data sources starting in 2020, which has slowly been released to Office versions via updates. You can read more in detail here:
form-based authentication in Office apps
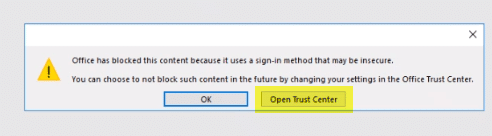
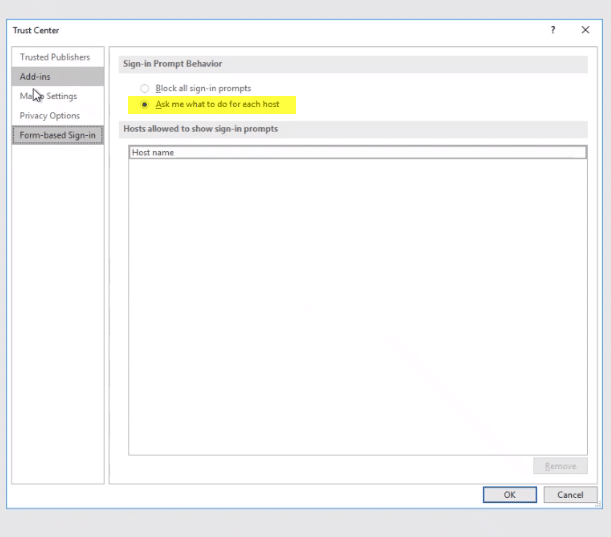
The process the user will need to complete is to open the trust center and choose the option to prompt and permit for each host.
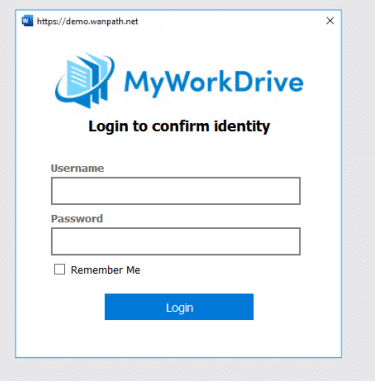
The next time the user opens a document, they will be prompted to add your MyWorkDrive server as an approved location
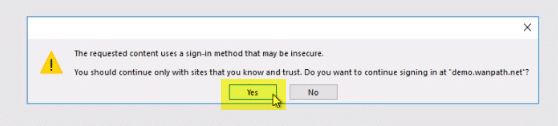
And then they will get the regular/expected login prompt to proceed to editing.
This is a one time process; once the server is trusted the user will only get the login when the session times out.
You may be able to push approved sources via group policy for domain joined machines, or via MDM for managed devices.
Setting paths as trusted locations
By setting a drive letter or path as a trusted location, you avoid the warning that a file has opened read only and editing must be enabled.
This can be done manually using the instructions noted above on a device by device basis, or you can use a GPO in Group Policy to push an update to domain joined devices.
Start by downloading the Group Policy templates for office from Microsoft.
https://www.microsoft.com/en-us/download/details.aspx?id=49030
After downloading them, run the executable and choose a location to store the files.
Transfer those files to the domain controller.
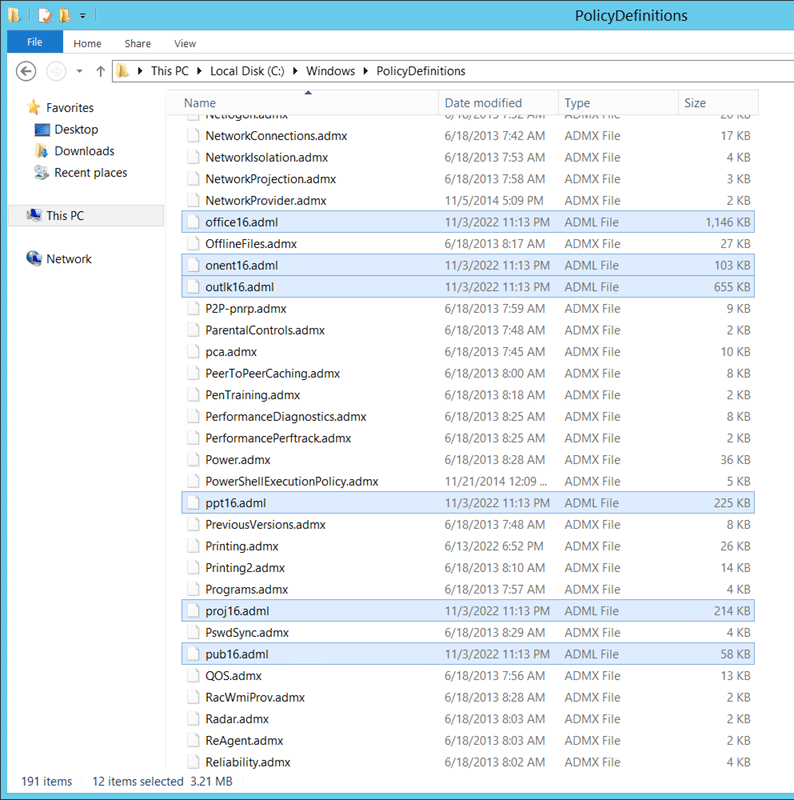
Connect to the domain controller, browse to the group policy template files, and move all those files to C:\Windows\PolicyDefinitions on the domain controller.
You may wish to select/copy only select files from the archive.
Next, open group policy management and create a new policy and link it to the desired OU.
Edit the new policy, then browse to:
User Configuration > Policies > Administrative Templates > Microsoft Word 2016 > Word Options > Security > Trust Center > and select Trusted Locations.
(note that you will have to set this policy for each office application)
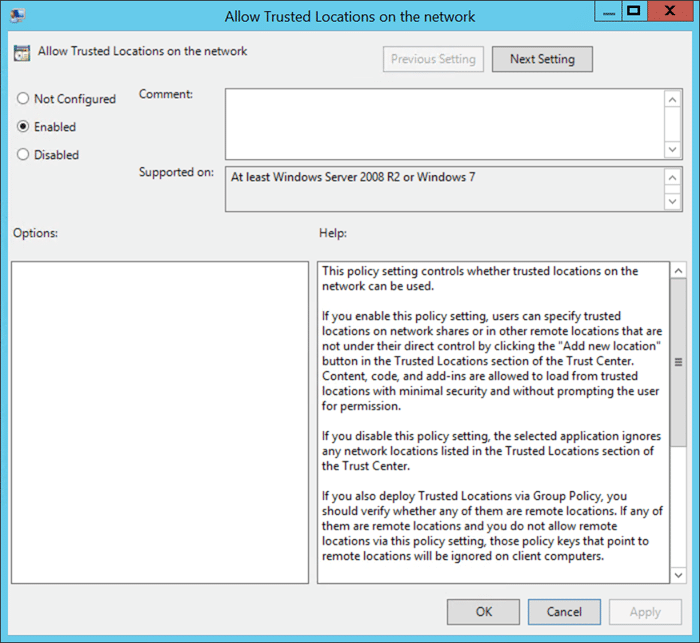
In the right pane, you will see several options. The option we are interested in is “Allow Trusted Locations on the network.” Double-click that option and choose “enable.”
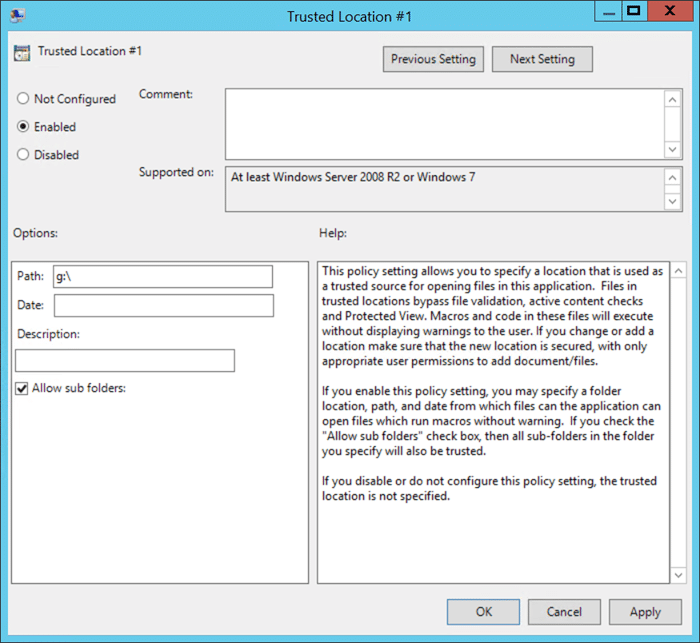
Next, add your network locations under trusted location and ensure “Allow sub folders:” is enabled and select Apply/OK. The drive letter will be the letter or letters you are are using for MyWorkDrive shares. If you are not specifying a drive letter on the server, the client default is typically W:, but can be changed client side.
Repeat this process for the rest of your Office applications by choosing the appropriate template.
After you have done this for all your applications, close the Group Policy Management Editor and ensure your new group policy is enabled.
The next time your users get group policy, your MyWorkDrive paths should be trusted and office documents will no longer be opened in protected view by default.