How can we help you today?
MyWorkDrive Active Directory Trust Support
The information and guidance in this article is only applicable when using MyWorkDrive on an Active Directory domain joined server with Active Directory for the user data. It is not applicable when installing MyWorkDrive in a directory-less environment with Entra ID identity for the user database.
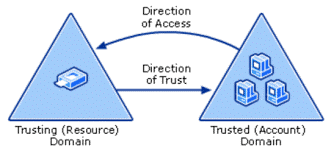
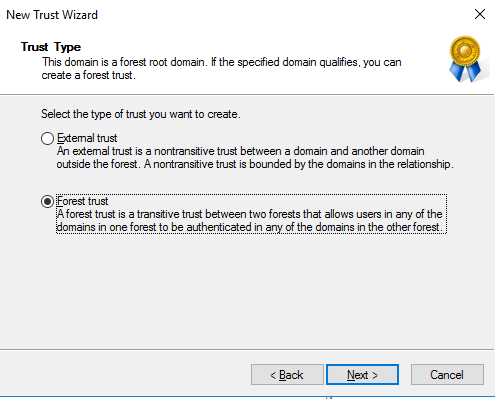
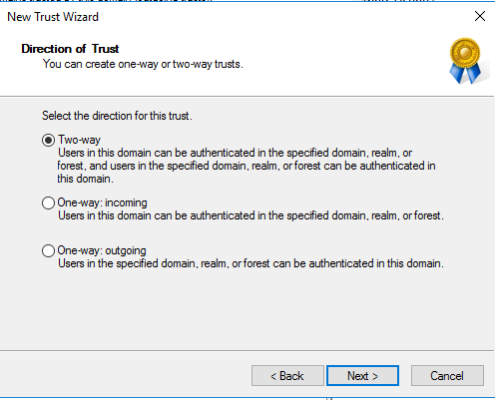
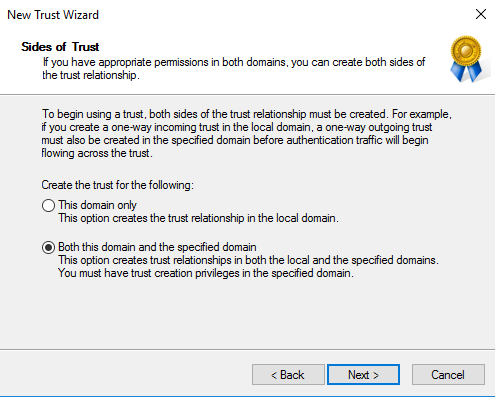
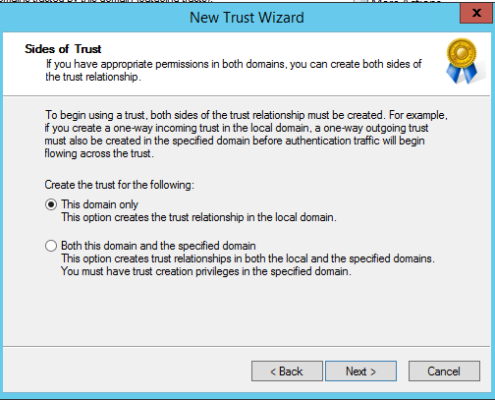
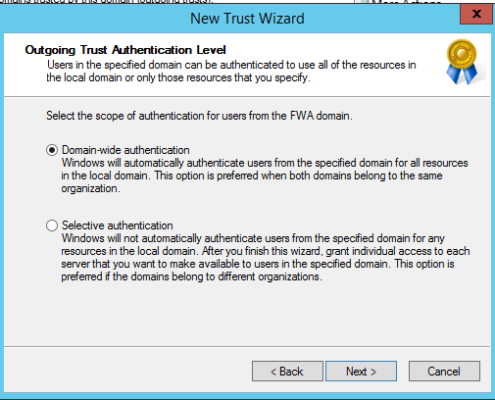
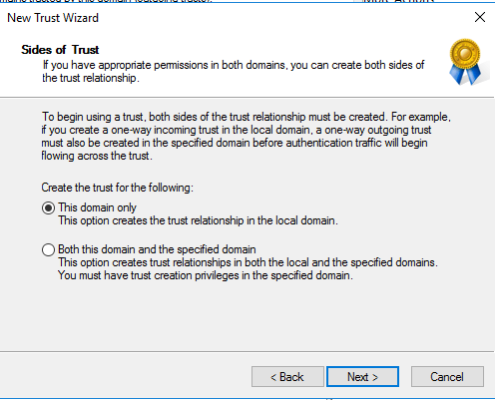
MyWorkDrive supports placement in an Active Directory Trust Resource Domain with the following limitations. SAML/SSO only works with Two-Way trusts. With One-Way trusts, Users can only login using Username/Password – SAML/SSO is not supported as it requires impersonating the user in the Trusted Account domain by the MWD Server located in the resource domain which is not permitted. Two Way trusts are the preferred option. Two Way trusts support selective authentication to limit permissions from the resource domain on the Trusted Account domain and can be adjusted as needed. *This article assumes the trusts are already active and any DNS conditional forwarders are in place.
MyWorkDrive Server Options required:
- Local groups are not supported and should be removed from NTFS Permissions or Shares – Use Domain based user security groups or users only.
- Domain Groups in the resource domain that contain users or groups in the trusted domain (groups in a group) are not supported or needed – add the trusted domain groups directly to NTFS Permissions on the share and in MyWorkDrive.
- To improve login speeds, move the Trusted Account domain to top of Domain Search Order on each MWD Server (settings, Domain Search Order).
- To improve login speeds a Trusted Account domain controller should be accessible via a fast, low latency network connection.
Contents
Two-Way Forest Trust Settings
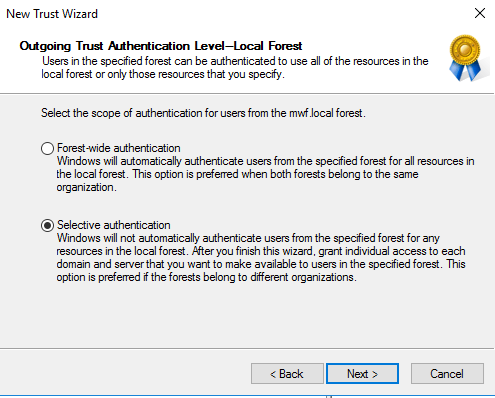
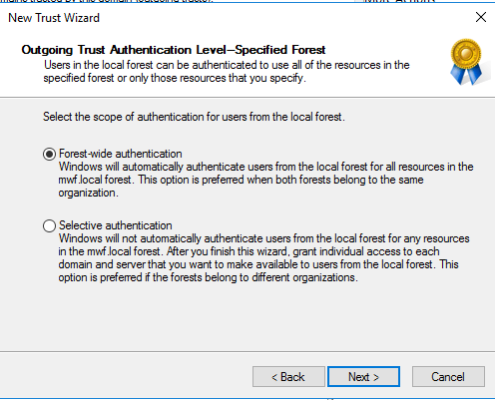
In this case the trust is created on the Trusted Account Domain DC (the customer) pointed to the Resource Domain (where the MWD Server lives). Two Way trusts support selective authentication to limit permissions from the resource domain on the Trusted Account domain.
With Two-Way trusts, Users can login using Username/Password or SAML/SSO. SAML/SSO is supported when the proper Delegation is setup to allow the MWD Server to impersonate users on any file servers located in the resource domain.
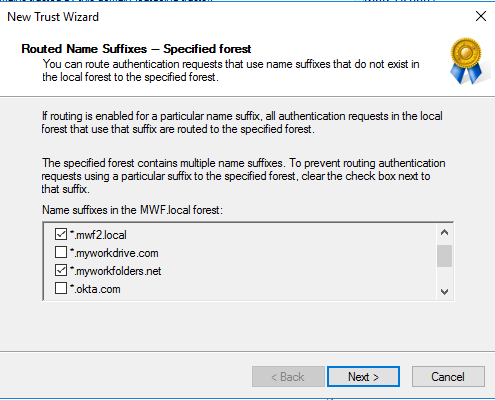
Login Name Formats Supported: FWA\Username, username@fwa.local, SamAccountName without domain: “Username” – when the User’s domain is added to top of MWD Domain Search Order, Email Address (alternate UPN Suffixes).
For purposes of this article the Active Directory Domains are as follows:
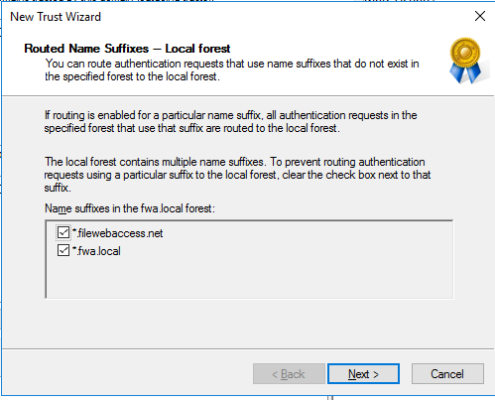
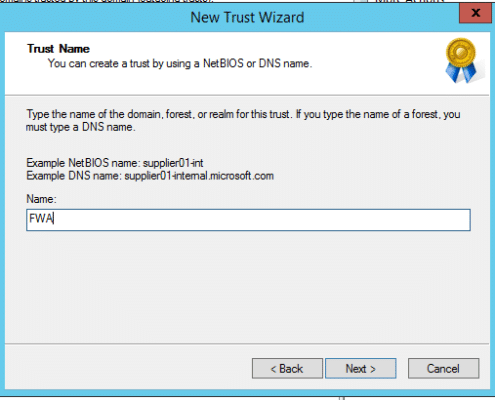
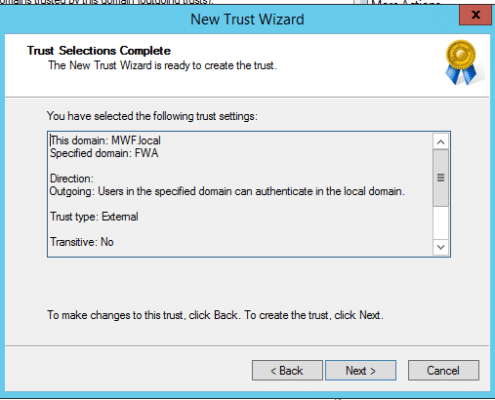
Trusted Account Domain: “FWA” FWA.local, filewebaccess.net
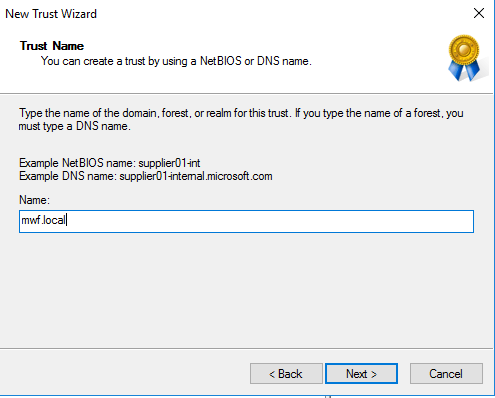
Resource Domain: MWF, MWF.local
Example Two Way Trust Settings:
One-Way External Domain Trust Settings
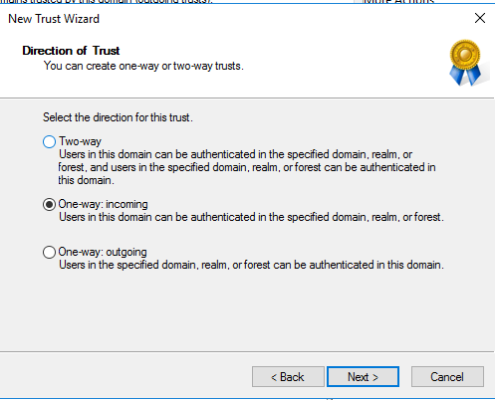
One-Way trusts only work with Username/Password login and require the following options/management settings:
- It is required that MyWorkDrive Server Administration be performed with an Account from the Trusted Account Domain (the resource domain account does not have permissions to read user/NTFS share User/Groups when editing/creating new shares).
- For one-way trusts, it is necessary to Add the Admin User Account from the Trusted Domain that will be used to Administer MyWorkDrive to the local administrators group on the MWD server to permit login to the MWD Admin Panel and manage shares
- For one-way trusts, Administration should be done after Logging into the MWD Admin panel to add/edit shares as the Trusted Account Domain User Administration account
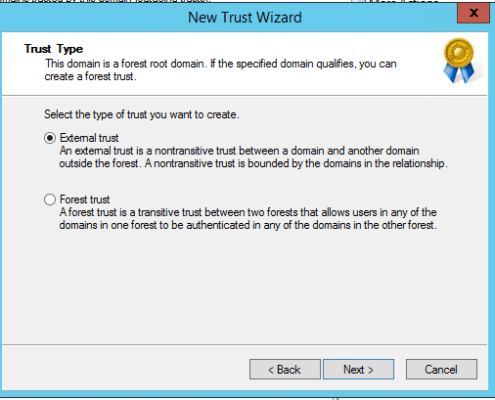
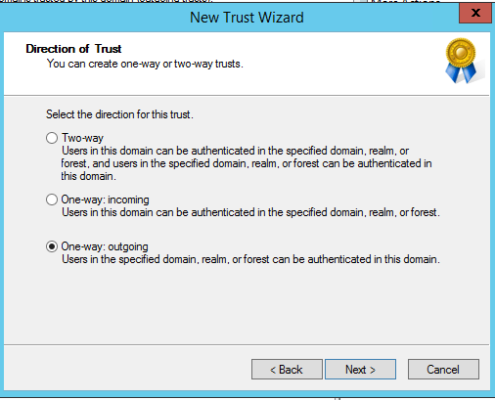
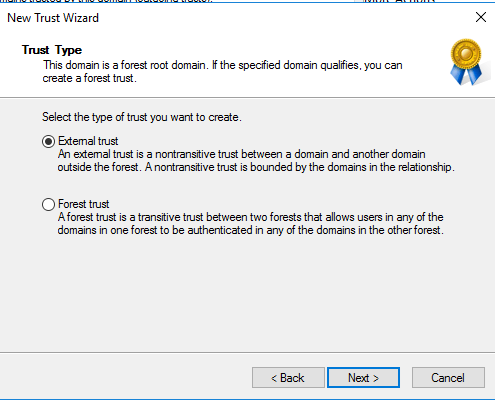
In this case we setup a one-way outgoing trust to the MWD resource domain using an external domain trust.
With One-Way trusts, Users can only login using Username/Password – SAML/SSO is not supported as it requires impersonating the user in the Trusted Account domain by the MWD Server located in the resource domain which is not permitted.
Login Name Formats Supported: FWA\Username, username@fwa.local, SamAccountName without domain: “Username” – when Trusted Account Domain is added to top of MWD Domain Search Order and username is unique across both domains.
Login Name Formats Unsupported: Email Address unless it matches the Account Domain root domain (alternate UPN Suffixes are not supported as there is no way to route domain name suffixes with external domain trusts)
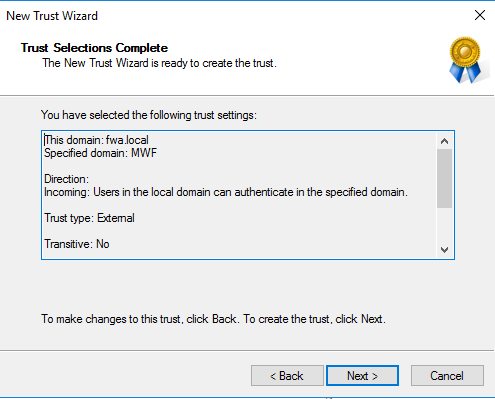
Example Resource Domain One-Way Outgoing Trust Settings:
This is created from the perspective of the MWD Resource domain DC to trust the Users domain.
Example Users Domain One-Way Incoming Trust Settings:
This is created from the perspective of the FWA Trusted Account domain DC to trust the Resource domain.