How can we help you today?
SAML Single Sign On Configuration – Okta
The instructions in this article are only applicable to MyWorkDrive installations using Active Directory for user identity. SAML SSO configuration is only required/supported when using Active Directory. Entra ID Installations use a native Microsoft login.
MyWorkDrive SAML Overview
Security Assertion Markup Language (SAML) is an open standard for exchanging authentication and authorization data between parties, specifically – between an identity provider and a service provider. As its name implies, SAML is an XML-based markup language for security assertions (statements that service providers use to make access-control decisions).
MyWorkDrive Server 5.1 introduced SAML based Web File Manager Single Sign On (SSO) in addition to ADFS (which is configured separately). For SAML, MyWorkDrive acts as a Service Provider (SP) while the SSO acts as the identity provider (IdP).
This document provides streamlined MyWorkDrive integration with Okta Single Sign-On starting with version 5.2. For version 5.0 or to manually configure SAML view our detailed SAML configuration article here
These instructions are also available online in the Okta application directory.
MyWorkDrive Okta Single Sign-On Setup
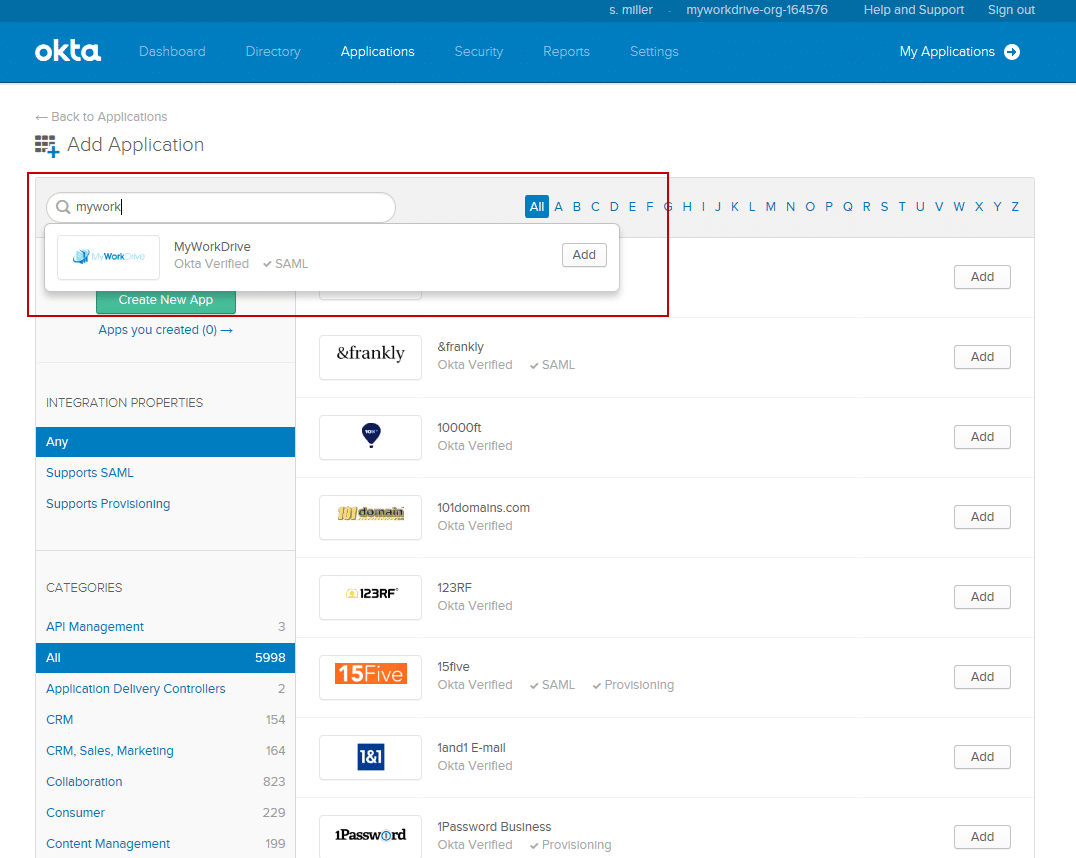
MyWorkDrive is listed an approved enterprise application in Okta. Just search for “MyWorkDrive” from the application search when adding the application.
The only information you will need to supply is your public URL to begin configuration.
Note our instructions below are streamlined and starting with MyWorkDrive Server version 5.2 we can simply input the “Identity Provider Metadata Url” URL from the Okta portal to automatically configure MyWorkDrive for Okta Single sign-on.
Okta SSO Prerequisites
- MyWorkDrive Server 5.2 or above.
- An Okta Account with Administrator privileges.
- Ensure users have a upn suffix applied for domain name to match the Okta Login name, so the users can login to your MyWorkDrive server with their email address.
- Ensure the MyWorkDrive server is trusted for delegation as per our Delegation Article
- Ensure your MyWorkDrive server is accessible on the internet for client login (web, mobile, map drive). Enable the Cloud Web Connector or Setup your own public SSL Certificate and Hostname pointing to your MyWorkDrive Server over port 443 (SSL) View Support Article.
Login Flow
The following explains the user login flow to MyWorkDrive from an identity provider (IdP):
- It is assumed all users are logging into the ldP using their UPN Suffix (eg @yourdomain.com) and it matches their Active Directory username UPN.
- Your MyWorkDrive server is using your own host name and SSL Certificate (*.MyWorkDrive.net is not supported for SAML).
- The user clicks the MyWorkDrive assertion consumer service URL (eg. https://YourMWDserver.yourdomain.com/SAML/AssertionConsumerService.aspx) as the single sign-on URL.
- If the user is not already logged into the ldP the MyWorkDrive server redirects the user to the SSL service to sign-in.
- Once confirmed the IdP service generates a valid SAML response and redirects the user back to MyWorkdrive to verify the SAML response.
- If the user authentication is successfully validated, they are automatically logged into their companies MyWorkDrive Web File Manager.
SAML MyWorkDrive Okta Configuration Steps
- Login to Okta with an Admin account and click the Admin button.
- From the Admin Dashboard, Click the “Add Applications” shortcut.
- In the “Search for an application” box, search for “MyWorkDrive” (no spaces). It will auto complete as you type. When you see the pane with our logo, click the Add button.
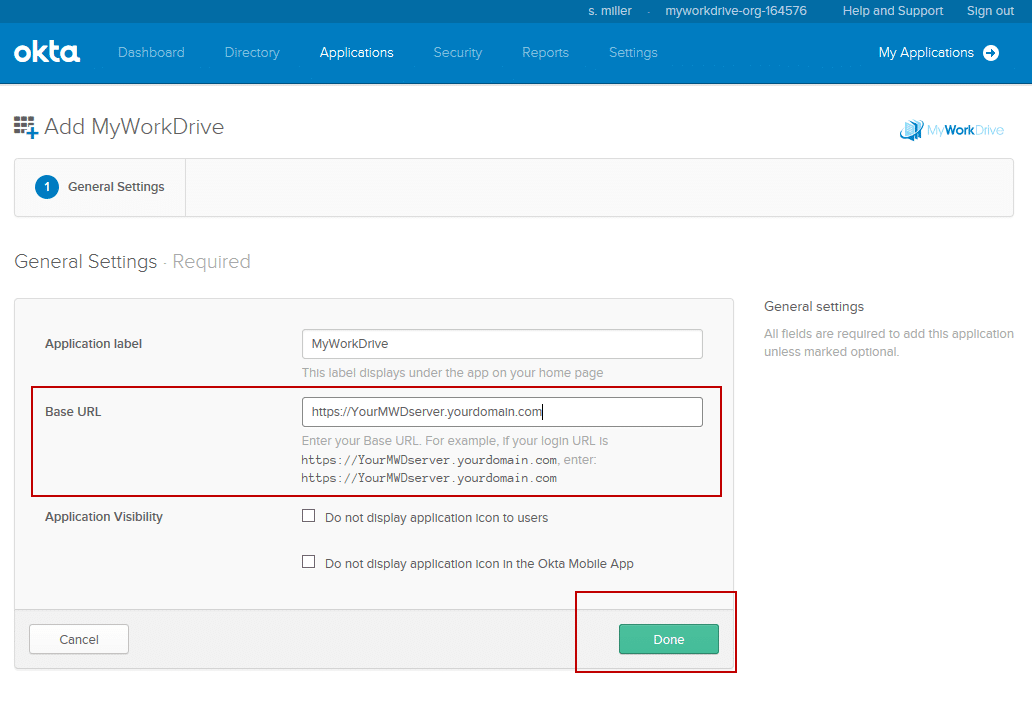
- The Application label should say “MyWorkDrive”
- In the Base URL field, type or paste the public URL as shown in the example, i.e. https://share.mycompany.com Note that SAML/SSO is not supported on our Cloud Web Connector using myworkdrive.net URLs.
- Optionally set Application Visibility options per your organization policy and click Done.
 Okta should now load the Application details page where you can assign the appropriate users/groups access. Okta will not work, however, until you complete setup in MyWorkDrive. We advise assigning at least one test user at this time.
Okta should now load the Application details page where you can assign the appropriate users/groups access. Okta will not work, however, until you complete setup in MyWorkDrive. We advise assigning at least one test user at this time.
 To complete Okta setup in MyWorkDrive you need to obtain the Identity Provider Metadata URL from Okta and enter it in MyWorkDrive.
To complete Okta setup in MyWorkDrive you need to obtain the Identity Provider Metadata URL from Okta and enter it in MyWorkDrive.
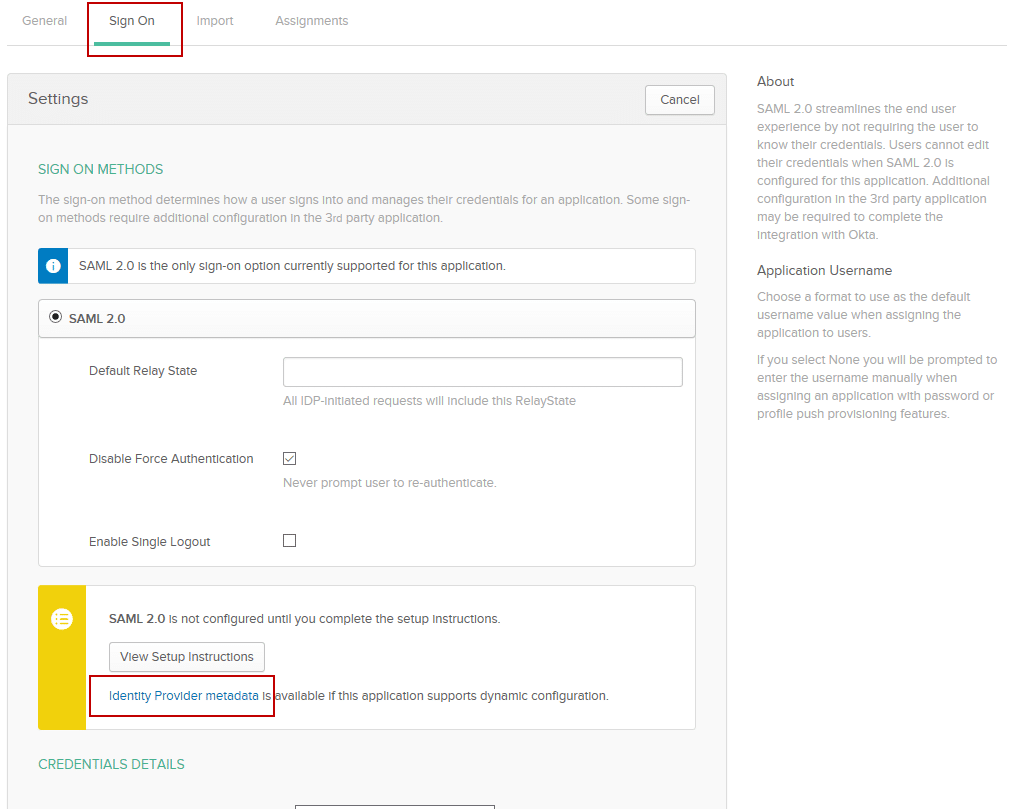
- Click on the Sign On tab from the Okta Application details page.
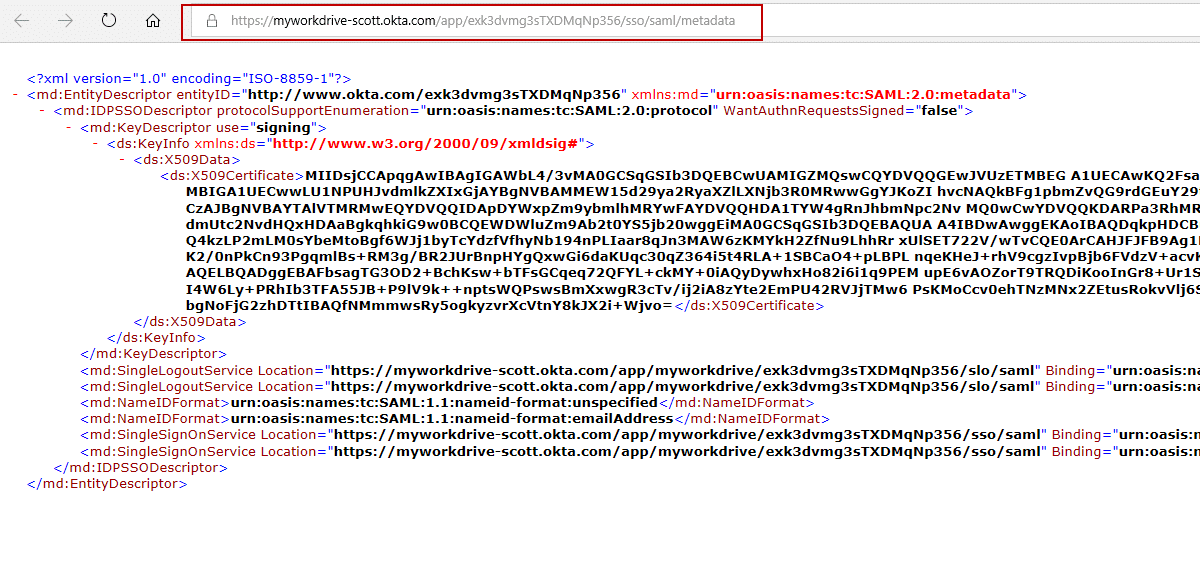
- Click on the link which says “Identity Provider Metadata.” This will open a new browser tab/window and show you the Metadata. You will need to enter (copy/paste) this URL into MyWorkDrive. Leave that window open for now.
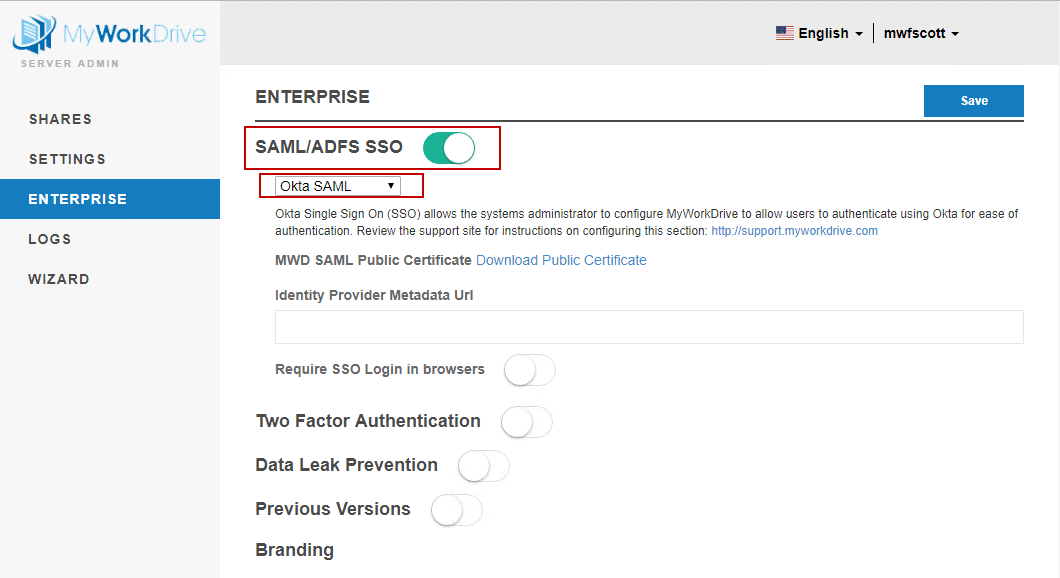
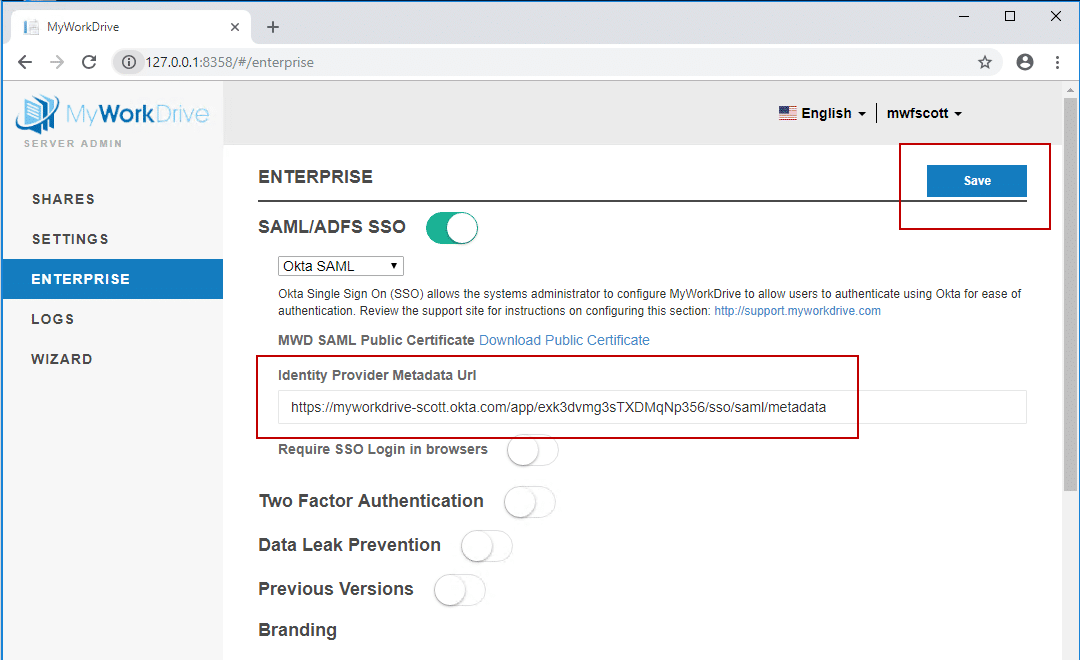
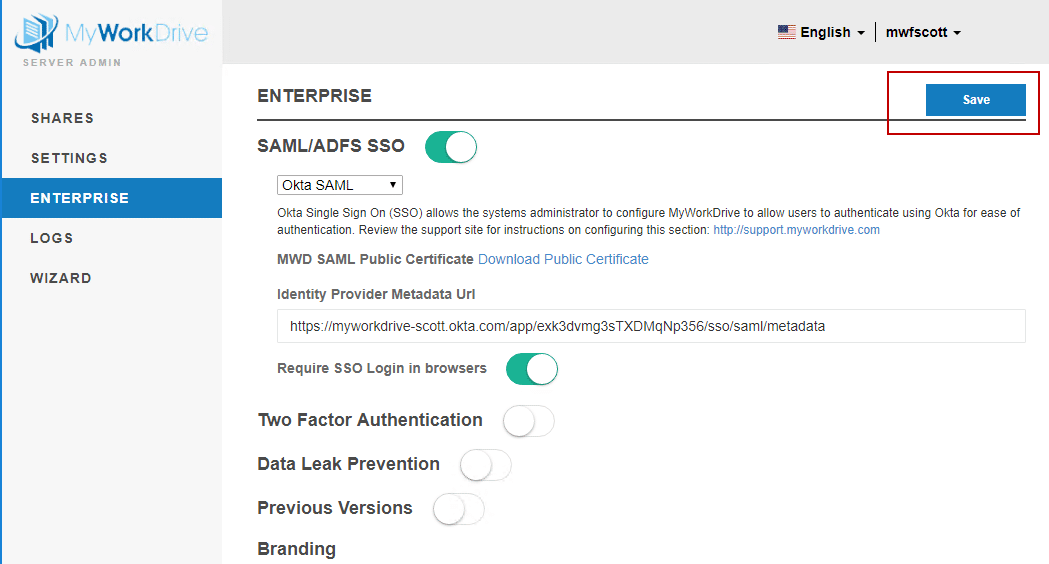
- Login to Admin for your MyWorkDrive Server and choose the Enterprise section.
- Enable the new SAML/ADSFS SSO option and select Okta SAML from the drop down. The Enterprise options section requires an Enterprise license.
- Enter the Identity Provider Metadata URL which you opened in a new browser window above.
The URL will look like https://myworkdrive-youroktaaccount.okta.com/app/exk3dvmg3sTXDMqNp356/sso/saml/metadata - Click Save.
- If you did not previously, assign a user to MyWorkDrive in Okta for testing with the appropriate UPN settings so their Okta login email address matches MyWorkDrive.
Test Access from Okta
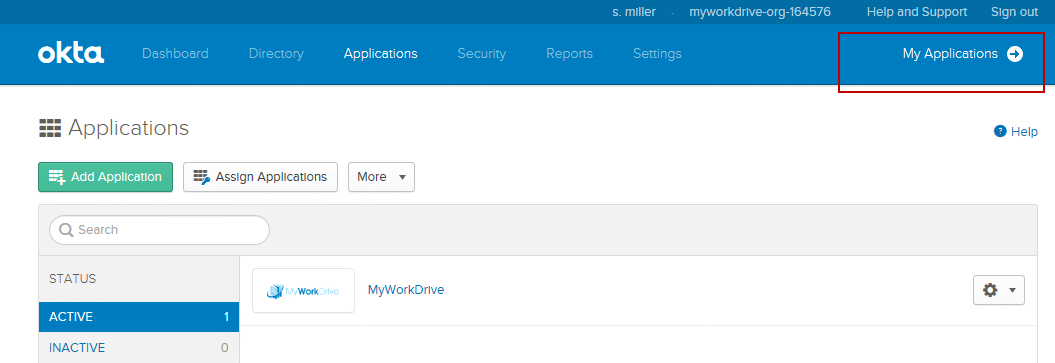
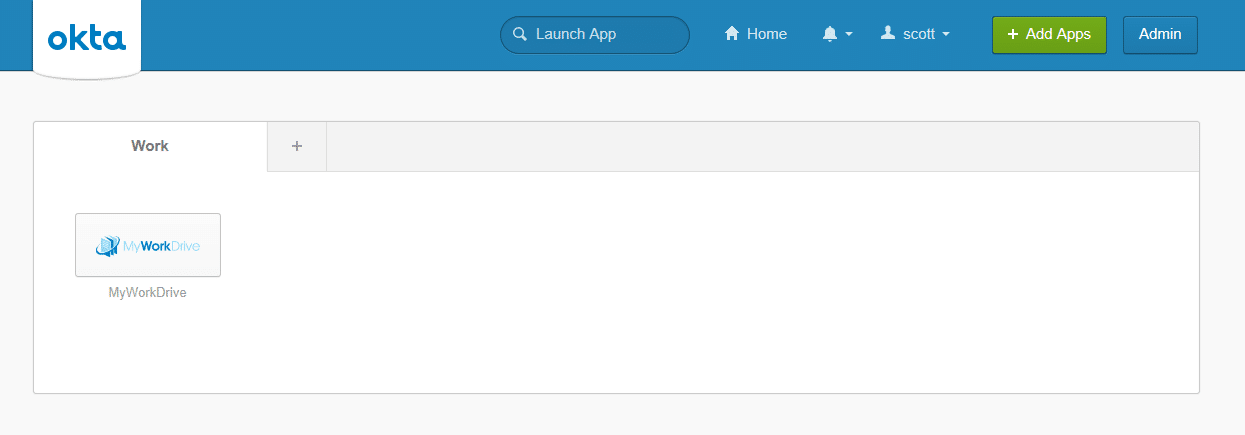
After assigning a test user, Login to Okta with your test user (or if using your own user, click on “My Applications” first to launch as a user instead of editing). Remember your Okta user login must match your MyWorkDrive login.
From the application list, click on the MyWorkDrive application (logo).
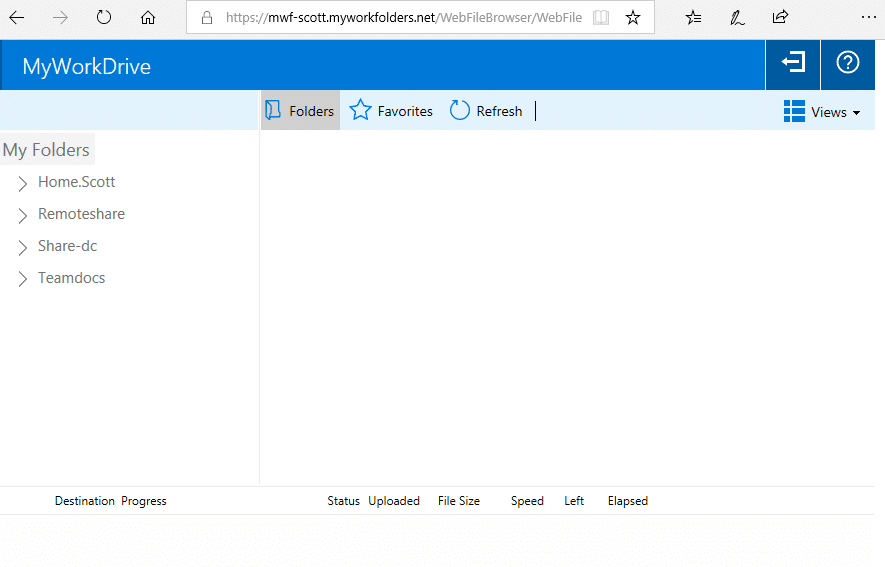
The user is automatically logged into your MyWorkDrive browser Web File Manager.
You have completed Okta SAML SSO setup for MyWorkDrive. You may now assign the rest of your users/groups as appropriate.
If you are missing shares in the folder list when logging in via the SAML Provider, the reason for that is missing or incorrect server delegation settings. Please ensure the MyWorkDrive server is trusted for delegation as per our Delegation Article.
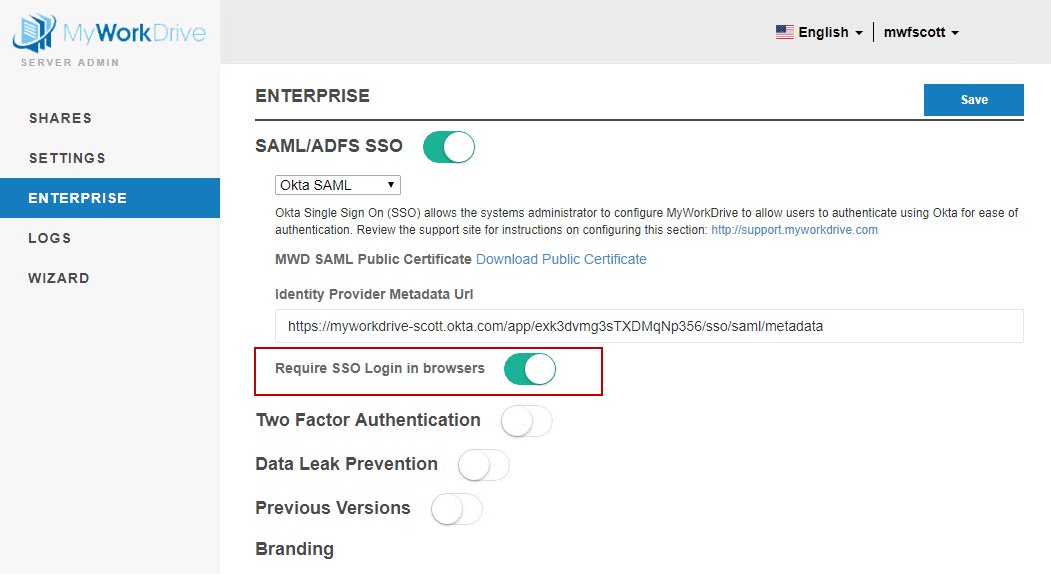
Optional Step – Require SSO Login in Browsers
If you wish to require users to Login to Web File Manager through Okta, select the option in My Work Drive Admin, Enterprise section for “Require SSO Login”
When this option is selected, the user will be prompted to Login to Okta if they are not logged in and access the MyWorkDrive Web File Manager.
If this option is not selected, users will be able to login via the regular login page, as well as by following the application link in Okta.
Optional Step – Single Logout
Single Logout will ensure that if a user logs out of Okta, they are also logged out of MyWorkDrive Web File Manager. There are several additional steps if you wish to configure Single Logout.
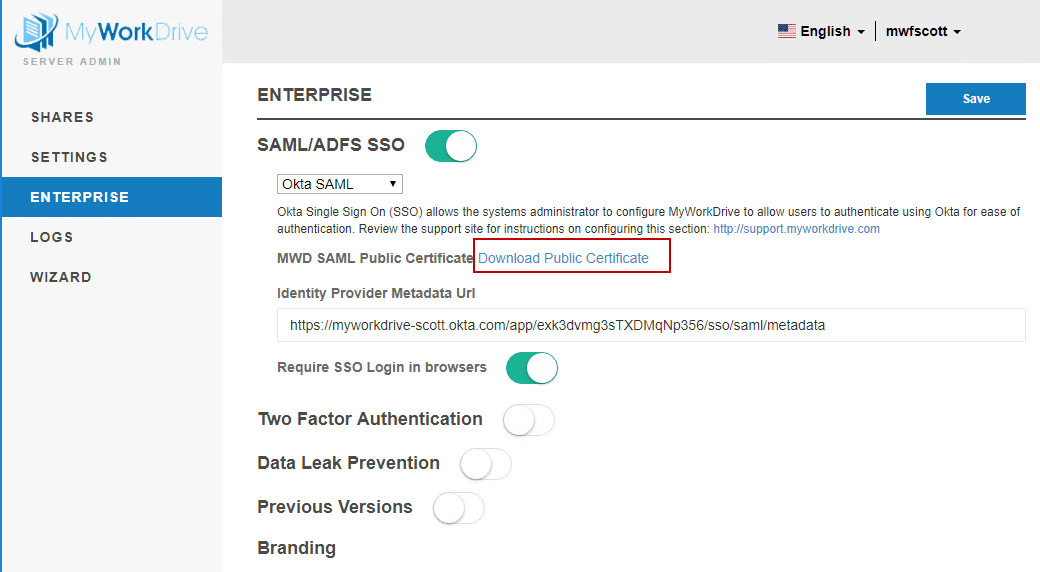
Download the Public Certificate from MyWorkDrive to your local machine. In the Admin Section, choose the Enterprise tab and if you have enabled SAML/ADFS SSO and selected Otka from the drop down, you will see the Download Public Certificate link. You’ll need to upload this in Okta in a subsequent step.
The download comes as a ZIP file. Locate this file (typically in Downloads) and extract the MWD.CER file
Now proceed to Okta.
- Login to Okta, Click on Admin to switch to the Admin View, then Applications and click on MyWorkDrive from the application list.
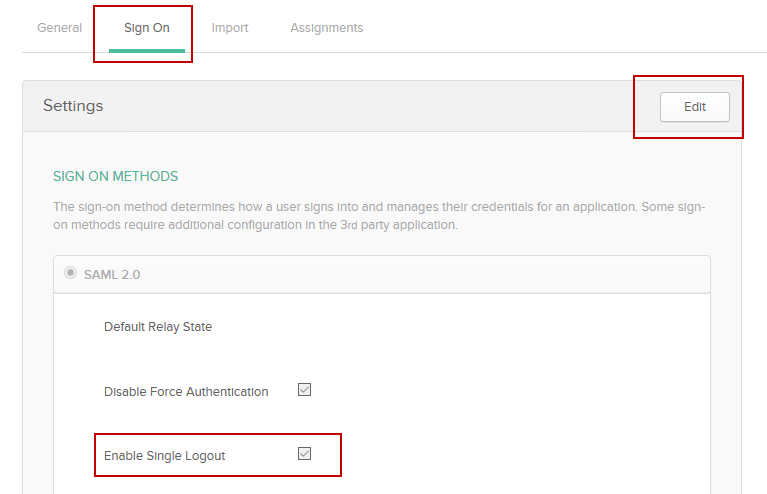
- Click on the “Sign On” tab, Click the Edit in the top right of the box.
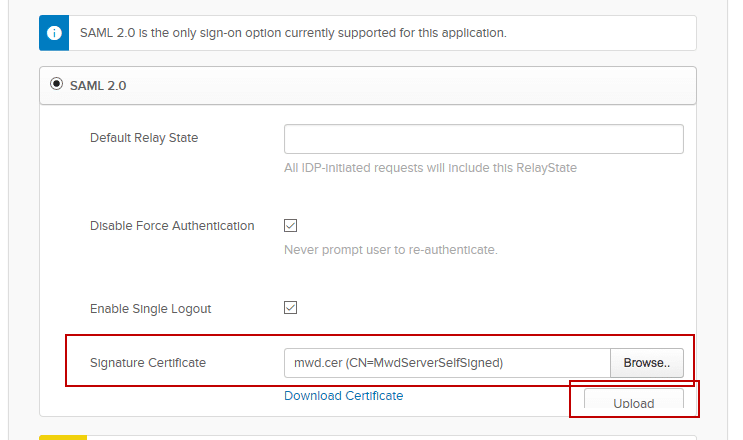
- Check the box for “Enable Single Logout”.
- This will expose the Signature Certificate box.
- Browse to the MWD.CER file you just extracted and upload it.
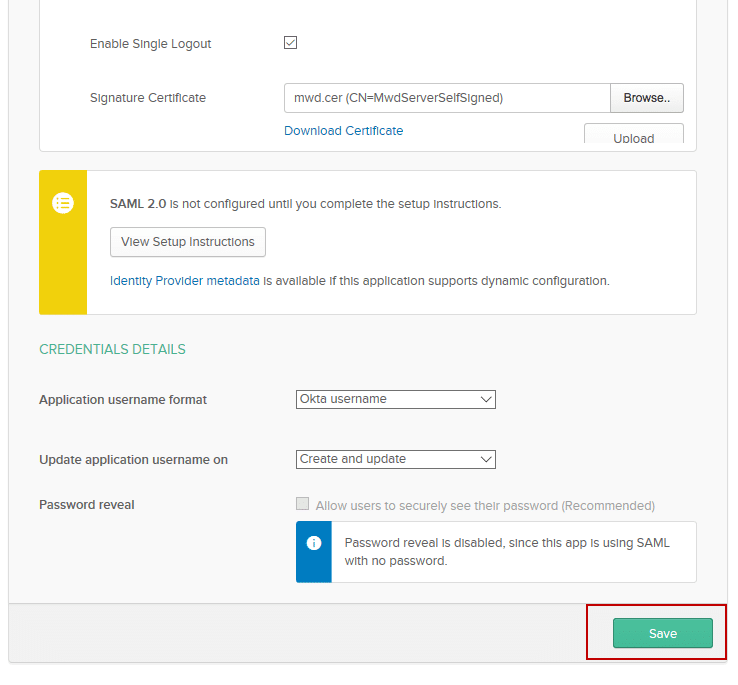
Scroll down and Click Save in the bottom right after uploading.
- The Okta portion of Single Logout setup is now complete.
Go Back to MyWorkDrive
- Load the Admin tools for MyWorkDrive.
- In the Enterprise section of MyWorkDrive Admin, click Save to refresh the MetaData in the Identity Provider Metadata URL, after you have enabled Single Logout, Uploaded the Certificate and Saved in Okta.
This will ensure your MyWorkDrive is updated via the Identity Provider Metadata URL with the logout URLs and certificate settings.
Congratulations, Single Logout is now enabled. Logging out of Okta will log you out of MyWorkDrive browser Web File Manager.