How can we help you today?
SAML Single Sign On Configuration – Rippling
Configuring MyWorkDrive for Rippling SSO
The instructions in this article are only applicable to MyWorkDrive installations using Active Directory for user identity. SAML SSO configuration is only required/supported when using Active Directory. Entra ID Installations use a native Microsoft login.
Contents
Preparation
MyWorkDrive is available as a configuration in Rippling.
You will need a few items from Rippling to configure MyWorkDrive. This should be available in Rippling in the SSO configuration section. You’ll start by creating new App in Rippling for MyWorkDrive
- The Rippling certificate (a .cer file)
- The Rippling Signin URL (this will look like https://www.rippling.com/api/platform/sso/sp-initiated/1111111111aaaaaaaaa22222222bbbbbb)
- The Rippling Service Provider name (This will be a URL like https://www.rippling.com/1111111111aaaaaaaaa22222222bbbbbb/idp.xml)
Once we have all these items, we can continue to the MyWorkDrive server for configuration.
MyWorkDrive Server Configuration
The first step of the process will be to copy the Rippling certificate to the MyWorkDrive server. Please copy the certificate to:
C:\Wanpath\WanPath.Data\Settings\SAML\Certificates
You may rename the file, but you should retain the .cer file extension
The second step is to configure the MyWorkDrive Server Admin Panel. After opening, navigate to the Enterprise tab.
- Enable SAML/ADFS SSO
- Select Manual SAML
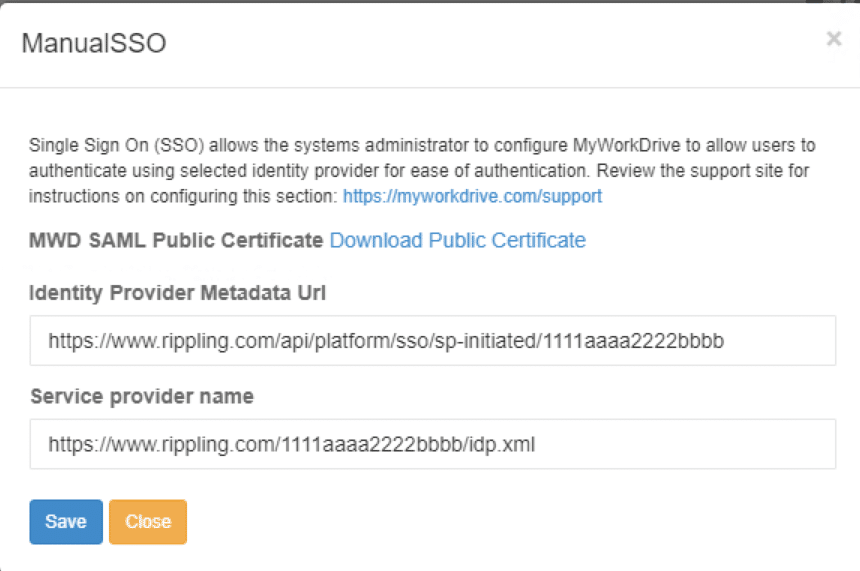
- Select “Enable connection”
- A pop-up will be presented requesting your Identity Provider Metadata Url and your Service provider name.
Rippling does not provide a metadata url, use the Signin URL for the metadata url.
Enter the service provider name url in the service provider field. - Select Save at the top of the page to save those settings.
The last step is to manually edit the saml.config file. Navigate to the following folder:
C:\Wanpath\WanPath.Data\Settings\SAML
Open the saml.config file with your preferred text editor. We will need to modify it to look like our example below:
<?xml version=”1.0″?>
<SAMLConfiguration xmlns=”urn:componentspace:SAML:2.0:configuration”>
<ServiceProvider Name=”MyWorkDrive”
Description=”MWD Service Provider”
AssertionConsumerServiceUrl=”~/SAML/AssertionConsumerService.aspx”
LocalCertificateFile=”C:\Wanpath\WanPath.Data\Settings\Certificates\mwd.pfx”
LocalCertificatePassword=”your-value-here”/>
<PartnerIdentityProviders>
<PartnerIdentityProvider Name=”https://www.rippling.com/1111aaaaa22222bbbb/idp.xml”
Description=”Rippling”
SingleSignOnServiceUrl=”https://www.rippling.com/api/platform/sso/sp-initiated/1111aaaa2222bbbb”
PartnerCertificateFile=”C:\Wanpath\WanPath.Data\Settings\SAML\Certificates\rippling.cer”/>
</PartnerIdentityProviders>
</SAMLConfiguration>
Configuration items for Rippling
- The AssertionConsumerServiceUrl will be entered in Rippling, and will be created based on your server’s hostname. https://YourMWDserver.yourdomain.com/SAML/AssertionConsumerService.aspx
- If prompted to uploader your MyWorkDrive certificate to Rippling the certificate can be found in C:\Wanpath\WanPath.Data\Settings\SAML\Certificates
both cer and pfx are available, and the password will appear in your saml.conf file (if needed)
User Accounts and Claims
MyWorkDrive expects the username to be passed as an email address, and expects it to match the logged in user’s UPN on Active Directory. If your users UPNs on AD are not their email addresses, you may need to write custom claim rules on Rippling to translate the user’s username to transform them to match your UPN on AD. Or update the UPN on AD.
Important Note:
MAKE A BACKUP! The saml.config file will be overwritten anytime the MyWorkDrive server settings are updated or the server is upgraded. This could result in your custom saml.config file being overwritten.